The renewable energy sector is experiencing unprecedented growth and digital transformation. However, this rapid evolution has created a perfect storm of cybersecurity vulnerabilities.
With 90% of the world’s largest energy companies experiencing breaches in 2023 alone, the need for robust cyber protection has never been more critical. As renewable energy infrastructure becomes increasingly connected, the attack surface expands, creating new opportunities for malicious actors.
This blog explores the unique challenges of operational technology cybersecurity in renewables and provides actionable strategies to strengthen your defenses against evolving threats.
The Growing Cybersecurity Crisis in Renewable Energy
The intersection of digital transformation and energy transition is creating unprecedented security challenges. Before diving into specific solutions, let’s understand what makes renewable energy systems particularly vulnerable.
The Convergence of Digital Transformation and Energy Transition
Renewable energy facilities are increasingly dependent on digital systems for monitoring, control, and optimization. Smart grids, IoT devices, and remote operations have revolutionized efficiency but expanded attack surfaces dramatically. A typical wind farm now contains hundreds of internet-connected devices, each representing a potential entry point for attackers.
Modern renewable facilities rely heavily on industrial cybersecurity systems that connect previously isolated operational technology to wider networks. This interconnectivity, while beneficial for operations, creates new vulnerabilities that cybercriminals are eager to exploit.
Understanding What is OT Cyber Security in Renewable Contexts
What is OT cybersecurity in the context of renewables? Unlike traditional IT environments that primarily protect data, operational technology (OT) cybersecurity focuses on systems that interact with the physical world. These include the control systems, sensors, and actuators that manage renewable assets like turbines, inverters, and battery storage systems.
The convergence of IT and OT systems has created complex environments where traditional security approaches often fall short. Understanding what is an operational technology environment is crucial – it’s a specialized ecosystem where availability and safety take precedence over confidentiality, and where system disruption can have immediate physical consequences.
The renewable sector faces unique challenges as cybersecurity for operational technology must address both legacy industrial control systems and cutting-edge IoT devices, often operating in remote locations with limited physical security. This complexity necessitates specialized approaches that go beyond conventional cybersecurity practices.
Critical Security Threats Targeting Renewable Energy Infrastructure
Renewable energy operators must understand the specific threats targeting their infrastructure before they can effectively defend against them. Let’s examine some of the most significant vulnerabilities.
Compromised SCADA and Industrial Control Systems
Control systems represent the most critical vulnerability in renewable operations. Attackers targeting SCADA systems can potentially disrupt power generation, damage equipment, or even create cascading failures across the grid. What makes these systems particularly vulnerable is their often outdated security architecture and increasing connectivity to external networks.
In 2015, attackers demonstrated the devastating potential of such breaches when they compromised Ukraine’s power grid, causing widespread outages. Similar techniques could be applied to renewable facilities with potentially catastrophic results. Protecting these systems requires multiple layers of defense and constant vigilance.
Supply Chain Security Vulnerabilities
The renewable supply chain introduces significant security risks through hardware, firmware, and software components. From compromised inverters to malicious code in monitoring solutions, attackers can exploit these vulnerabilities to gain persistent access to critical systems.
Addressing these risks requires rigorous vendor assessment, secure procurement practices, and ongoing monitoring of deployed assets. As renewable deployments accelerate, supply chain security becomes increasingly crucial to maintaining operational integrity and preventing backdoor access to critical infrastructure.
Remote Access Exploitation
Remote monitoring and management capabilities are essential for distributed renewable assets but create significant security challenges. These systems often rely on internet-facing interfaces that, if compromised, provide direct access to operational technology.
Understanding what an OT environment helps in appreciating why traditional remote access solutions may be inadequate. OT environments have unique requirements for availability, safety, and deterministic behavior that demand specialized security approaches. Securing these connections requires robust authentication, encrypted communications, and strict access controls designed specifically for operational contexts.
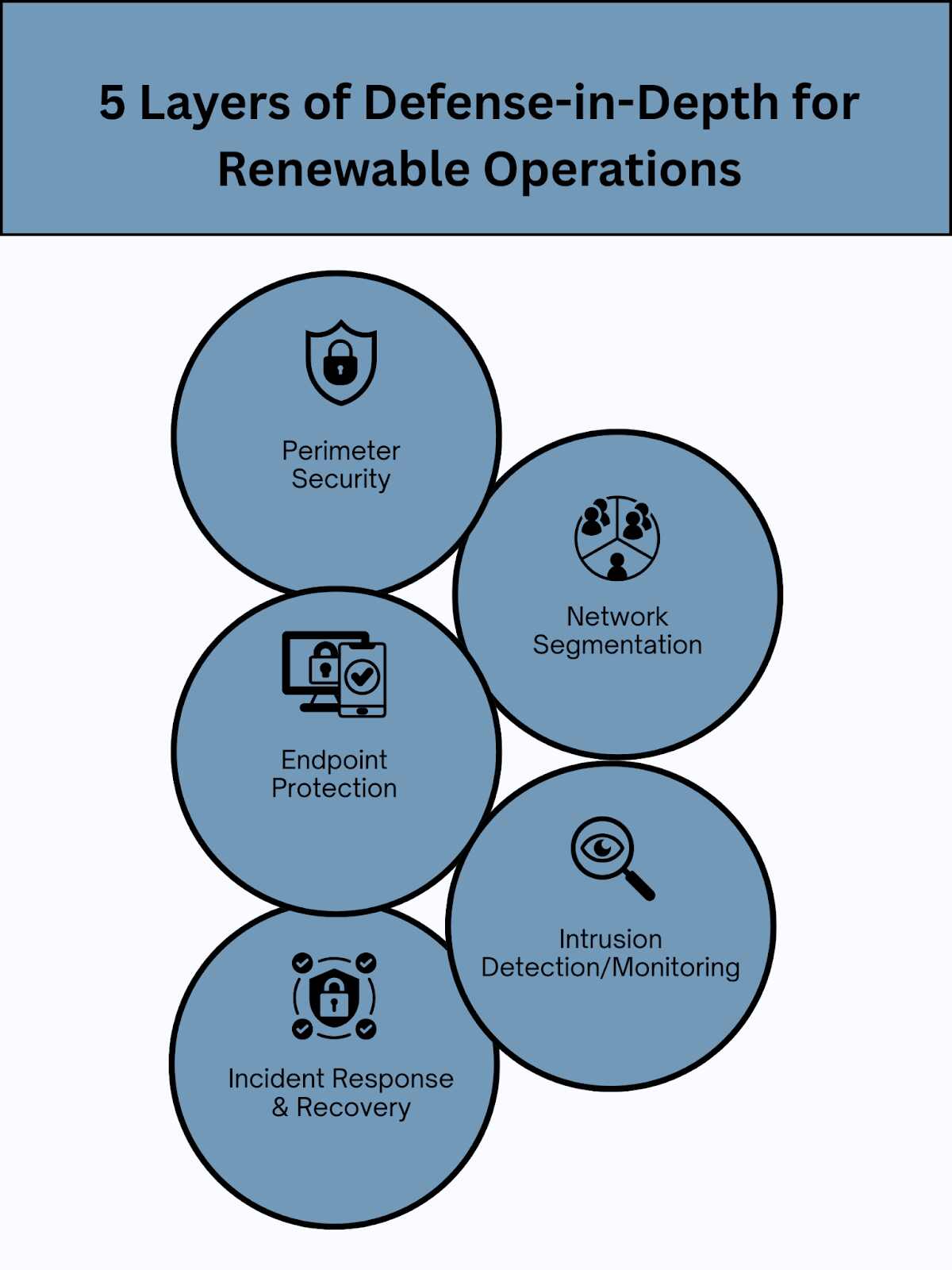
Strategic Approaches to Strengthen Your Renewable Energy Cyber Resilience
Now that we’ve identified the primary threats, let’s explore practical strategies for enhancing cyber resilience in renewable energy operations.
Implementing Defense-in-Depth for Renewable Infrastructure
A layered security approach provides multiple barriers that attackers must overcome, significantly reducing the risk of successful breaches. This strategy combines network segmentation, endpoint protection, monitoring, and response capabilities to create a comprehensive defense.
For renewable operations, defense-in-depth must extend from corporate networks to field devices, creating zones of protection around critical assets. This approach recognizes that no single security measure is infallible and ensures that the failure of one control doesn’t compromise the entire operation.
Securing Cloud-Logger Platforms and Remote Monitoring Systems
Cloud-based monitoring platforms represent both an opportunity and a vulnerability for renewable operators. While they enable efficient management of distributed assets, they also create potential attack vectors if not properly secured.
Implementing strong access controls, encryption, and continuous monitoring for these platforms is essential. Additionally, renewable operators should establish secure communication protocols between field devices and cloud platforms, ensuring that operational data remains protected throughout its lifecycle.
Modernizing Legacy OT Systems in Renewable Deployments
Many renewable facilities incorporate legacy operational technology that wasn’t designed with cybersecurity in mind. Addressing these vulnerabilities requires a strategic approach that balances security improvements with operational stability.
OT security standards like IEC 62443 provide frameworks for securely integrating and upgrading legacy systems. These standards establish processes for risk assessment, system design, implementation, and ongoing maintenance that address the unique challenges of operational technology in renewable environments.
Building Cyber Resilience Through System Redundancy
Resilience goes beyond prevention to ensure that operations can continue even when attacks occur. For renewable energy providers, this means designing systems with redundant components, fail-safe modes, and rapid recovery capabilities.
Implementing architectural approaches that limit the impact of compromised systems can significantly reduce downtime and potential damage. This might include air-gapping critical components, implementing manual overrides, or developing operational procedures that maintain essential functions during cybersecurity incidents.
The Future of Renewable Energy Cybersecurity
The cybersecurity landscape for renewable energy continues to evolve rapidly. Looking ahead, several key trends will shape how the industry approaches these challenges.
Emerging Technologies Reshaping Industrial Cybersecurity
-
AI-powered threat detection, zero-trust architectures, and secure-by-design principles are revolutionizing OT cybersecurity.
-
These technologies enable proactive defense by identifying and mitigating threats before they impact operations.
-
When applied correctly, they can enhance both cybersecurity and operational efficiency.
-
Effective implementation requires deep knowledge of both cybersecurity fundamentals and the operational needs of renewable energy systems.
Building a Sustainable Security Talent Pipeline
-
There’s a growing shortage of cybersecurity professionals with OT-specific expertise in the renewable sector.
-
Closing this gap requires specialized training and stronger collaboration between IT and OT teams.
-
Organizations investing in internal talent development will gain a strategic edge in securing their infrastructure.
-
Training should focus on both technical skills and the business/safety requirements unique to renewable energy operations.
Wrapping Up
The renewable energy transition is transforming our energy landscape, but it must be accompanied by a parallel evolution in cybersecurity practices. By implementing robust OT security standards and developing comprehensive defense strategies, renewable operators can protect their assets and contribute to a more resilient energy future.
As digital technologies continue to reshape the renewable sector, cybersecurity must be viewed not as an obstacle but as an enabler of safe, reliable operations. Organizations that embrace this perspective will be better positioned to navigate the complex challenges of the clean energy transition while maintaining the security and integrity of critical infrastructure.
FAQs
1. What makes renewable energy systems uniquely vulnerable to cyberattacks compared to traditional energy infrastructure?
Renewable systems rely on interconnected IoT devices, remote operations, and legacy control systems, creating a larger, more complex attack surface that traditional IT security measures often can’t fully protect.
2. How can renewable energy operators secure remote monitoring systems without compromising operational efficiency?
Operators should implement encrypted communications, multi-factor authentication, role-based access control, and real-time monitoring to ensure secure remote access while maintaining efficient asset management.
3. Why is defense-in-depth critical for protecting operational technology in renewable energy?
Because no single security measure is foolproof, layering multiple defenses—like segmentation, endpoint protection, and anomaly detection—helps mitigate risks and contain potential breaches across complex renewable networks.
